In today’s increasingly digital world, the need for secure and unbreakable encryption is more important than ever. With the rise of quantum computing, traditional cryptographic methods are at risk of being compromised, highlighting the need for quantum-resistant techniques. In this blog post, we will delve into the fascinating world of quantum computing and the vulnerabilities it poses to traditional cryptography. We will explore the need for quantum resistance in our encryption methods and discuss the emerging quantum-resistant cryptographic techniques that are being developed to combat this threat. Additionally, we will examine the importance of implementing quantum-resistant standards to ensure the security of our digital communications and transactions. Join us as we unpack the impact of quantum resistance in cryptography and the steps being taken to safeguard our data in the age of advancing technology.
Understanding Quantum Computing
Quantum computing is a hot topic in the world of technology and cryptography. It represents a fundamental change in computing and has the potential to revolutionize multiple industries. Unlike traditional computers that operate using bits, which can either be 0 or 1, quantum computers use quantum bits or qubits, which can be both 0 and 1 at the same time due to the principles of superposition and entanglement. This allows quantum computers to perform complex calculations at an incredibly fast rate, making them ideal for tasks that are currently impossible for classical computers to handle.
One key aspect of quantum computing is its ability to solve certain problems more efficiently than classical computers. For example, quantum computers are anticipated to be able to crack certain encryption methods that are currently considered unbreakable using conventional computers. This is why many are concerned about the potential threat quantum computing poses to the security of data and communications.
Understanding the basics of quantum computing is essential for anyone involved in the technology or cryptography realms. It is important to grasp the fundamental principles behind quantum computers, as well as their potential impact on the future of cybersecurity. By staying informed about quantum computing, individuals can stay ahead of the curve and proactively address potential security challenges that may arise in the future.
As technology continues to advance, so does the need for a deeper understanding of quantum computing. With the potential for massive computational power and security breaches, it’s crucial for individuals and organizations to gain knowledge about this emerging technology and prepare for the potential changes it may bring.
Vulnerabilities of Traditional Cryptography
Traditional cryptography, although widely used for securing data and communications, is not without its vulnerabilities. One of the main vulnerabilities of traditional cryptography is its reliance on mathematical problems that can be solved with enough computing power.
For example, the widely used RSA algorithm relies on the difficulty of factoring large prime numbers, but with the advent of quantum computers, this problem becomes trivial to solve using Shor’s algorithm. This means that any data encrypted using RSA can easily be decrypted by a quantum computer, rendering the encryption useless.
Another vulnerability of traditional cryptography is the reliance on symmetric key algorithms, such as AES, which can be broken using brute force attacks if the key length is not sufficiently long. As computing power increases, the time it takes to perform a brute force attack decreases, making it easier to crack encrypted data.
Additionally, traditional cryptography is vulnerable to man-in-the-middle attacks, where an attacker intercepts and alters communications between two parties without their knowledge. This can compromise the confidentiality and integrity of the data being transmitted, highlighting the need for more secure cryptographic techniques.
The Need for Quantum Resistance
In today’s digital age, the threat of quantum computing to traditional cryptographic methods has become a pressing concern for cybersecurity experts. As quantum computing continues to advance at a rapid pace, the security of sensitive data is at risk as classical cryptographic techniques are susceptible to being cracked by powerful quantum algorithms.
With the potential to break widely used encryption schemes such as RSA and ECC, the need for quantum resistance in cryptographic systems has never been more urgent. As quantum computers have the ability to solve complex mathematical problems at an unprecedented speed, the existing cryptographic infrastructure must evolve to withstand this new threat.
It is imperative for organizations and governments to proactively address the vulnerabilities of traditional cryptography and invest in quantum-resistant standards to ensure the long-term security of sensitive information. Without the integration of quantum-resistant cryptographic techniques, the potential ramifications of quantum computing on data security could be catastrophic.
As the race towards achieving quantum resistance in cryptography intensifies, the adoption and implementation of new cryptographic standards are essential for safeguarding digital assets in the era of quantum computing.
Quantum-Resistant Cryptographic Techniques
As the era of quantum computing dawns upon us, traditional cryptographic techniques are facing unprecedented challenges. The immense processing power of quantum computers has the potential to break the most widely used encryption algorithms, such as RSA and ECC. This has led to the urgent need for quantum-resistant cryptographic techniques that can withstand the onslaught of quantum attacks.
One of the most promising approaches to achieving quantum resistance is through the development of post-quantum cryptography. Post-quantum cryptographic techniques, also known as quantum-resistant or quantum-secure algorithms, are designed to be immune to the algorithms that quantum computers are expected to break.
Several post-quantum cryptographic techniques have been proposed, including lattice-based cryptography, code-based cryptography, multivariate polynomial cryptography, and hash-based cryptography. These techniques rely on mathematical problems that are believed to be hard even for quantum computers to solve. By using these quantum-resistant cryptographic techniques, organizations can future-proof their systems against the threat of quantum attacks.
Implementing quantum-resistant cryptographic techniques requires a concerted effort from the industry, academia, and standards bodies. The development of quantum-resistant standards is crucial to ensure interoperability and compatibility across different systems and platforms. It is imperative for organizations to start transitioning towards quantum-resistant cryptographic techniques to safeguard their data and communications from future quantum threats.
Implementing Quantum-Resistant Standards
As the development of quantum computing continues to progress at a rapid pace, the need for implementing quantum-resistant standards in the field of cryptography has become increasingly crucial. Traditional cryptographic techniques, which have been the cornerstone of secure communication and data protection for decades, are now facing serious vulnerabilities due to the potential threat posed by the immense computing power of quantum systems.
One of the key challenges in implementing quantum-resistant standards lies in the development of cryptographic algorithms and protocols that can withstand attacks from quantum computers. In response to this pressing concern, researchers and industry experts have been actively working on designing and testing new cryptographic techniques that are resistant to the cryptographic capabilities of quantum computers.
Another important aspect of implementing quantum-resistant standards is the need for collaboration and cooperation among the global cryptographic community. It is crucial for stakeholders such as government agencies, academic institutions, and industry players to work together in establishing and adopting quantum-resistant cryptographic standards to ensure the integrity and security of sensitive data and communications in a quantum-powered world.
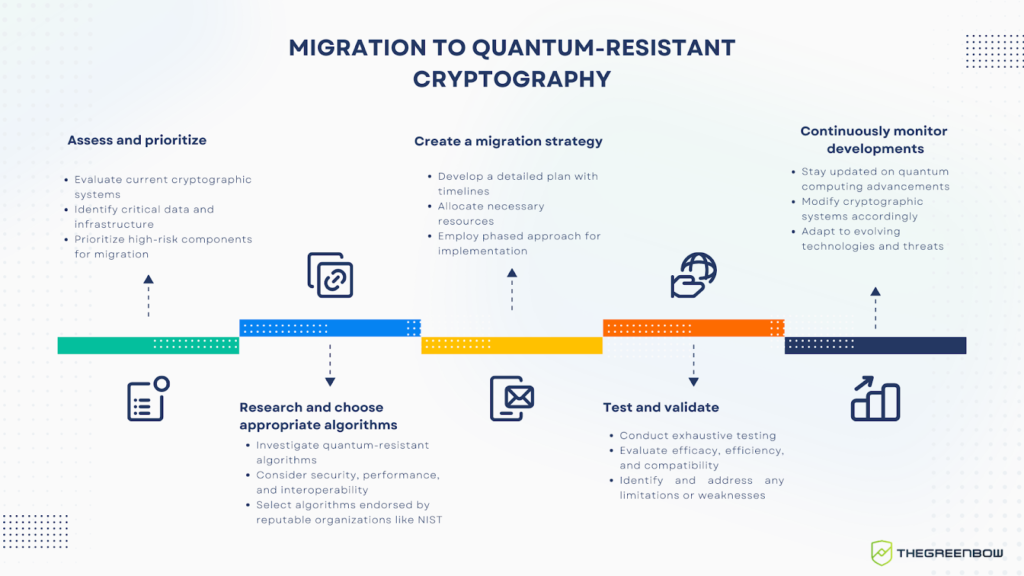
Furthermore, the implementation of quantum-resistant standards requires a proactive approach towards transition and migration strategies. Organizations and businesses need to assess and update their existing cryptographic systems to align with quantum-resistant cryptographic techniques in order to protect their sensitive information from potential security breaches and attacks.
Frequently Asked Questions
What is quantum computing?
Quantum computing is a type of computing that takes advantage of the strange ability of subatomic particles to exist in more than one state at any time and potentially perform millions of computations at once.
How does quantum computing impact cryptography?
Quantum computing has the potential to break traditional cryptographic techniques, as it can solve complex mathematical problems much faster than classical computers.
What are the vulnerabilities of traditional cryptography to quantum computing?
Traditional cryptographic techniques, such as RSA and ECC, rely on mathematical problems that can be easily solved by quantum computers using algorithms like Shor’s algorithm.
Why is there a need for quantum-resistant cryptography?
With the advancements in quantum computing, there is a growing need for cryptographic techniques that can resist attacks from quantum computers and provide long-term security for sensitive data.
What are some quantum-resistant cryptographic techniques?
Post-quantum cryptography, lattice-based cryptography, hash-based cryptography, and multivariate-quadratic-equations are some of the quantum-resistant cryptographic techniques being developed and standardized.
How can organizations implement quantum-resistant standards?
Organizations can start by updating their cryptographic protocols and algorithms to those that are quantum-resistant, and stay informed about the latest advancements in post-quantum cryptography.
What’s the future outlook for quantum resistance in cryptography?
As quantum computing continues to advance, the need for quantum-resistant cryptographic standards will become more critical, and researchers and organizations will continue to work on developing and implementing such techniques to secure data in the quantum era.